Auth Codes
Fundamentally, information is secured by the organization. When information needs to be restricted to a subset of the population within an organization, users can request for the creation of an auth code. The auth code acts as a lock and key. The lock is created with keys provided to specific users. As the lock is applied to information, only those individuals with both organizational access and the keys will be able to access the information.
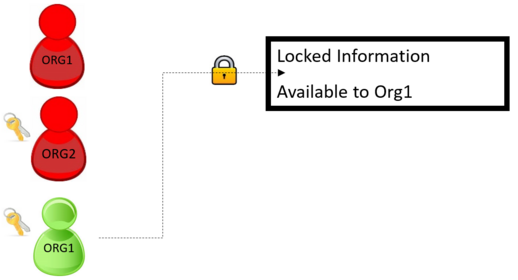
This mechanism is typically used by Contracts and Procurement to protect sensitive information that would otherwise be visible to everyone within BHP and HBJV.
Additive Auth Codes
In the same way that you can bolt a door with multiple locks or have locked cabinets in locked rooms, you can use multiple auth codes on a single piece of information. To access the information, the users would need to have the keys to all the locks. In practice C&P have implemented this architecture to further segregate users with access to sensitive information to strictly sensitive information that pertains to packages pertinent to the user.
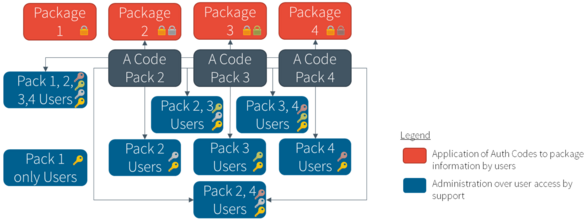
Refer to C&P Auth Codes to learn more about the auth codes that have established for control over Contracts and Procurement data.